By Kato Mivule
To understand what a Process Control Block (PCB), we first take a look at what a Process is. A Process is a computer program in execution.[1] A computer program therefore must be active to be considered a process. Whenever a Process gets to runs in the operating system, it alters its state. The State of a Process is current status in activity of that program. [2]
Every Process that is executed is in one of the following States: [1] [2]
New: In this status, the Process is just made or created.
Running: In the Running status, the Process is being executed.
Waiting: The process waits for an event to happen for example an input from the keyboard.
Ready: In this status the Process is waiting for execution in the CPU.
Terminated: In this status the Process has finished its job and is ended. However, if the Process is terminated before if finishes executed, it is said to be killed.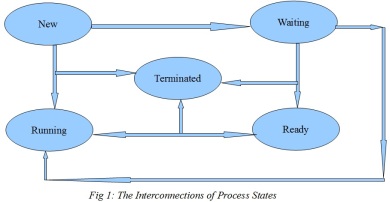
According to Silberschatz et al, processes in operating systems are delineated by a process control block (PCB) also known as the task controlling block or the task struc.[1] [3] The PCB is the data structure that stores data about a Process in the operating system. [4]
Silberschatz et al notes that a process control block in an operating system will at least have the following information: [1]
Process State: information about the current state of the process, from new, ready, running, to terminated.
Program Counter: states the location for the next command to be run for the same process.
CPU Register: state information on various types of registers is stored during interrupts for continuity to occur correctly when process resumes.
Memory Management Information: state data on memory is stored such as page tables, limit registers, or segment tables.
Accounting Information: stores state data on values of CPU and real time utilized, time limits, account numbers, job or process numbers.
I/O Status Information: Data on list of I/O devices apportioned to the process, a list of open files etc.
Therefore all major operating systems should at least have the above structure tailored to their unique process control block architectures.
According to Francesc Solsona et al, in the Linux operating system, the process control block is an implementation of a double linked list data structures. Francesc Solsona et al further state the fields associated with the Linux PCB as follows: [6]
policy: scheduling policy which include normal task policy and real-time policies.
rt_priority: responsible for planning between real time processes.
priority – ”static” priority: responsible for planning for normal processes.
counter, “dynamic” normal tasks priority.
files: open files structure, saves data about the job open files.
freq: sending and receiving message frequency.
A look at the Ubuntu Linux Process Manager, the System Monitor keeps track of the following data on processes running in the operating system:
Process Name: name of the process running
Status: current state of process, from sleeping to active.
Percentage of CPU: how much CPU resources are being used by process.
Nice:
Process ID:
Memory: memory usage.
Waiting Channel: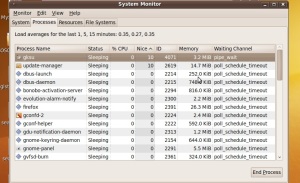
Fig 2: Ubuntu’s System Monitor
In the Windows operating system, Shibu gives a good description of the Task /Process Manager obligated for mounting the Process Control Block (PCB)or the Task Control Block (TCB) as referred to by Shibu. [6] Shibu further explains that the TCB or the PCB is used to store data associated with a particular process with the undermentioned content:[6]
ID: stores ID data of any particular process.
State: stores data on the actual status of the process, from ready, waiting, to terminated.
Type: keeps track if a process is real-time or normal.
Priority: keeps track on the priority of the process.
Context Pointer: context pointer
Memory Pointer: pointer to code memory, data memory, stack memory for the process.
System Resource Pointers: pointers to system assets.
Process Pointers: pointers to other PCBs
In Windows operating system, the Windows Task Manager is responsible for managing processes in the operating system. Windows Task Manager keeps the following data on Processes and Services:
Under processes:
Image Name: Name of Process.
User Name: User using the Process.
CPU: keeps track of CPU resources used by the process.
Memory: keeps track of memory usage by process.
Description: keeps a brief description of the process being used.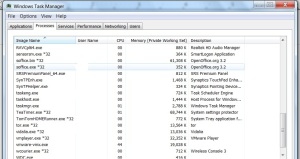
Fig 3: Windows Task Manager for Processes
Under services:
Name: name of services being used.
PID: Process ID.
Description: brief description of service in use.
State: current status of services, either running or stopped.
Group:
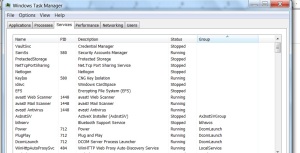
Fig 3: Windows Task Manager for Services
References
[1] Abraham Silberschatz, Greg Gagne, Peter Baer Galvin, “Operating System Concepts 8th Edition Binder Ready Version”. John Wiley & Sons, 2008, ISBN 978 0470 128725, Page 101-102.
[2] “Process states – Wikipedia, the free encyclopedia.” [Online]. Available: http://en.wikipedia.org/wiki/Process_states. [Accessed: 11-Sep-2010].
[3] “Process control block – Wikipedia, the free encyclopedia.” [Online]. Available: http://en.wikipedia.org/wiki/Process_control_block. [Accessed: 12-Sep-2010].
[4] Nell Dale, John Lewis. “Computer Science Illuminated, Edition 4″. Jones & Bartlett Learning, 2009, ISBN 0763776467, 9780763776466, Page 601.
[5] Cameron Hughes, Tracey Hughes. “Parallel and distributed programming using C++,Edition illustrated”. Addison-Wesley, 2004, ISBN 0131013769, 9780131013766, Page 39.
[6] José M. L. M. Palma. “High performance computing for computational science – VECPAR 2002: 5th international conference, Porto, Portugal, June 26-28, 2002 : selected papers and invited talks Volume 2565 of Lecture notes in computer science”. Springer, 2003, ISBN 3540008527, 9783540008521, Page 598-599.
[7] Shibu KV. “Intro To Embedded Systems 1E”. Tata McGraw-Hill, ISBN 007014589X, 9780070145894, Page 387.